Unified Payments Interface (UPI) has revolutionized digital payments in India, enabling instant, seamless transactions via mobile devices. Developed by the National Payments Corporation of India (NPCI) and regulated by the Reserve Bank of India (RBI), UPI powers millions of daily transactions, merging multiple banking features into a single platform. However, its widespread adoption has also attracted cybercriminals, leading to a surge in frauds like phishing, social engineering, and money laundering. To combat these threats, Open-Source Intelligence (OSINT) tools tailored for UPI systems have emerged as critical assets in cybersecurity. These tools leverage publicly available data to monitor transactions, detect fraud, and investigate cybercrimes, ensuring the integrity of mobile payment ecosystems.
This article explores the role of UPI OSINT tools in cybersecurity, focusing on their applications in fraud detection, digital forensics, threat intelligence, and risk mitigation. We’ll also examine how a hypothetical cybersecurity firm, Cybergliknet, could develop or deploy such tools to secure UPI platforms, using a sample UPI OSINT data output as a case study. By harnessing OSINT, organizations can proactively safeguard UPI systems, protect user data, and maintain trust in digital payments.

Understanding UPI and Its Cybersecurity Challenges
UPI is an instant real-time payment system that allows users to link multiple bank accounts to a single mobile application, facilitating inter-bank transactions. Key features include:
Since its launch in 2016, UPI has seen exponential growth, with digital payment volumes rising by 216% from March 2019 to March 2022, according to the RBI. However, this growth has also exposed vulnerabilities, making UPI a prime target for cybercriminals.

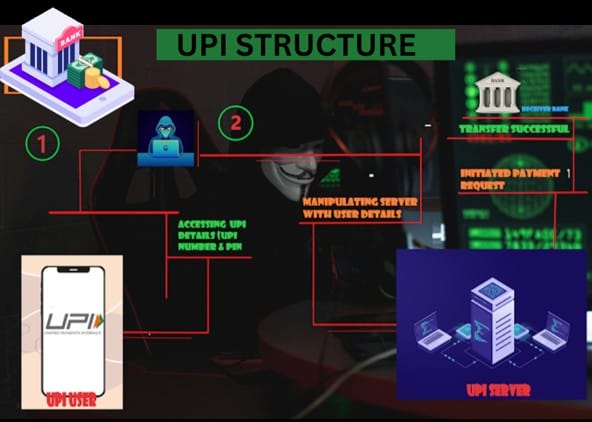
The rapid expansion of UPI has outpaced regulatory frameworks, creating gaps that fraudsters exploit. Common UPI frauds include:
These threats undermine financial integrity, erode user trust, and pose risks to national security by funding illicit activities like organized crime or terrorism. Addressing them requires advanced tools like UPI OSINT solutions.

The Role of OSINT in UPI Cybersecurity
Open-Source Intelligence (OSINT) involves collecting, analyzing, and interpreting publicly available data from sources like social media, websites, forums, news articles, and public databases. In cybersecurity, OSINT is used to:
Unlike classified intelligence, OSINT relies on legally accessible data, making it cost-effective and transparent. For UPI systems, OSINT tools can analyze transaction patterns, user behavior, and digital footprints to detect and mitigate risks.
UPI OSINT tools are specialized software or platforms designed to monitor and analyze publicly available data related to UPI transactions. While specific tools from companies like Cybergliknet may not be publicly documented, their hypothetical capabilities include:
These capabilities make UPI OSINT tools invaluable for financial institutions, cybersecurity firms, and law enforcement agencies.

While Cybergliknet may not be a widely recognized entity in public records, we can hypothesize it as a cybersecurity firm specializing in OSINT solutions for mobile payment systems like UPI. Based on the provided sample data, Cybergliknet could be associated with a UPI ID (cybergliknet@okaxis) linked to IDFC FIRST Bank, suggesting it operates within India’s financial ecosystem. Its offerings might include:
The following sample output demonstrates how a UPI OSINT tool by Cybergliknet might analyze a UPI ID to gather publicly available banking details, aiding fraud investigations or due diligence:
🕵🏻 UPI ID Check Success! =========================== 📱 UPI ID: cybergliknet@okaxis =========================== 👤 Name: Blink Hack 🏦 Bank: IDFC FIRST Bank 🔠 IFSC Code: IDFB0040101 🔠 MICR Code: 400751002 🏛️ Branch: BKC-NAMAN CHAMBERS BRANCH 📍 District: MUMBAI 🌆 State: MAHARASHTRA 🏠 Address: GROUND FLOOR NAMAN CHAMBERS, C-32, G-BLOCK, BANDRA-KURLA COMPLEX, BANDRA EAST, MUMBAI 400051 📞 Contact: +9122424235XX 💳 UPI: True 💸 RTGS: True 💰 NEFT: True 💵 IMPS: True 🌍 SWIFT: None 🏙️ City: MUMBAI 🏢 Centre: MUMBAI 🗺️ ISO3166: IN-MH 🏦 Bank Code: IDFB
This data, likely sourced from public banking directories or APIs, provides insights into the account holder’s identity, bank details, and transaction capabilities. For example, cybersecurity professionals could use this to:
Applications of UPI OSINT Tools
UPI frauds, such as phishing or QR code scams, often leave digital footprints in public domains. OSINT tools can:
For instance, if a UPI ID like cybergliknet@okaxis is repeatedly associated with collect requests from unknown sources, the tool could flag it for review.

In case of a UPI-related security breach, OSINT tools aid investigations by:
For example, the sample data above could help investigators confirm the bank and branch associated with a suspicious UPI ID, aiding in tracking the account holder.
UPI OSINT tools enhance threat intelligence by:
To reduce UPI vulnerabilities, OSINT tools can:
Challenges and Ethical Considerations
Conclusion
UPI OSINT tools are transforming cybersecurity for mobile payment systems like UPI, offering powerful capabilities for fraud detection, digital forensics, threat intelligence, and risk mitigation. A hypothetical firm like Cybergliknet could lead the way by developing specialized tools that monitor UPI transactions, trace cyberattacks, and protect financial ecosystems. The sample UPI OSINT data illustrates how such tools can provide actionable insights, from verifying UPI IDs to supporting investigations.
As UPI continues to dominate India’s digital payment landscape, the need for robust cybersecurity measures grows. By leveraging OSINT, organizations can stay ahead of fraudsters, safeguard user trust, and ensure the security of mobile transactions. For more information on Cybergliknet’s offerings or specific UPI OSINT tools, contacting the company directly or visiting their official website would provide deeper insights into their solutions.
References
Subscribe to our newsletter for the latest cybersecurity news, tips, and updates.